[ad_1]

Context:
As per reports of some national and international news agencies there appeared on a leaked list of “potential” or actual targets for spying by the Israeli company NSO’s Pegasus spyware.
Recently, it has been reported that Pegasus, the malicious software, has allegedly been used to secretly monitor and spy on an extensive host of public figures in India.
As per claims, at least a 1,000 Indian phone numbers are in a list of potential targets of surveillance using the Pegasus spyware sold by Israeli company the NSO Group to “vetted governments” with the approval of the Israeli government.
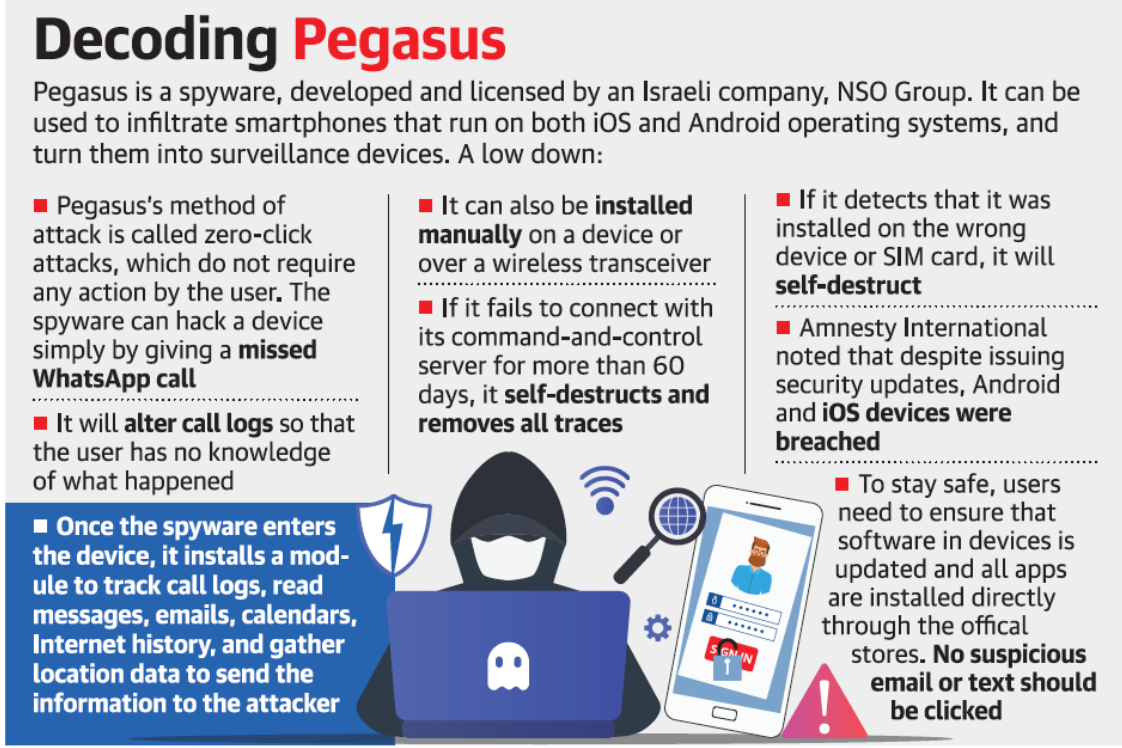
About Pegasus Spyware:
- Pegasus works by sending an exploit link, and if the target user clicks on the link, the malware or the code that allows the surveillance is installed on the user’s phone.
- A presumably newer version of the malware does not even require a target user to click a link.
- Once Pegasus is installed, the attacker has complete access to the target user’s phone.
- Pegasus can “send back the target’s private data, including passwords, contact lists, calendar events, text messages, and live voice calls from popular mobile messaging apps”.
- The target’s phone camera and microphone can be turned on to capture all activity in the phone’s vicinity, expanding the scope of the surveillance.
What information can be compromised?
- Once infected, a phone becomes a digital spy under the attacker’s complete control.
- Upon installation, Pegasus contacts the attacker’s command and control (C&C) servers to receive and execute instructions and send back the target’s private data, including passwords, contact lists, calendar events, text messages, and live voice calls (even those via end-to-end-encrypted messaging apps).
- The attacker can control the phone’s camera and microphone, and use the GPS function to track a target.
- To avoid extensive bandwidth consumption that may alert a target, Pegasus sends only scheduled updates to a C&C server.
- The spyware is designed to evade forensic analysis, avoid detection by anti-virus software, and can be deactivated and removed by the attacker, when and if necessary.
Is Surveillance has legal backing?
- There are legal provisions for intercepting communication and accessing digitally stored information in the interests of national security and public safety.
- The capture of a handheld machine by Pegasus turns that into a real-time spy on the target who can be watched over and followed every step.
- This surveillance is total, into their private and intimate lives, which have no bearing on any public interest.
- Information obtained illegally may have been used to compromise institutions, to steal elections, sabotage Opposition campaigns, and even dislodge an Opposition government.
- Indian citizens were indeed targets of a vicious, abominable and uncivil surveillance campaign by a government entity, Indian or foreign.
- Lack of awareness and specialists in digital security makes this a vulnerable sector.
- Terrorists and other anti-social elements have started using more of cyberspace which provides them with more getaways.
Cyber Security Framework in India:
- Cyber security has become an integral aspect of national security. Moreover, its area of influence extends far beyond military domains to cover all aspects of a nation’s governance, economy and welfare.
- With countries resorting to digital warfare and hackers targeting business organisations and government processes, India has to create awareness that not a single person or institution is immune to it.
- While the government and the corporate world are better placed perhaps to create their own programs, it is the civil society who needs to bring into this ambit.
- Educational institutions including central universities, private universities, industry associations, Industrial Training Institutes (ITIs) must incorporate courses on cybersecurity.
- Given the future of technology under Industrial Revolution 4.0, India requires a strong cybersecurity framework based on the 4D principles i.e. Deter, Detect, Destroy and Document, so that it can sub verse all attempts towards any cyber challenges.
- Given increasing dominance of mobile and telecommunication, both National cyber security policy and National Telecom Policy will have to effectively coalesce to make a comprehensive policy for 2030.
Safe Cyber security: Indian Cyber Crime Coordination Centre (I4C):
- The Indian Cyber Crime Coordination Centre (I4C) was recently inaugurated by the government. National Cyber Crime Reporting Portal has also been launched pan India.
- It is a citizen-centric initiative which will enable citizens to report cybercrimes online and all the complaints will be accessed by the concerned law enforcement agencies for taking action as per law.
- The portal specifically focuses on crimes against women, children, particularly child pornography, child sex abuse material, online content pertaining to rapes/gang rapes, etc.
- It also focuses on crimes like financial crime and social media related crimes like stalking, cyberbullying, etc.
- It will improve the capacity of law enforcement agencies to investigate the cases after successful completion by improving coordination amongst the law enforcement agencies of different States, districts and police stations.
Conclusion:
The whole incident brought forward the issue of digital security and the ways to achieve it with minimum loopholes.
It is necessary to be self-aware about digital security because compromise in that could lead to a situation of total surveillance.
Setting stringent cybersecurity standards to protect individuals and institutions of national importance, to make sure that the unity of the nation and the integrity of the individuals stay safe and secure.
The largest democracy in the world cannot be at the mercy of a shady, private company.
[ad_2]